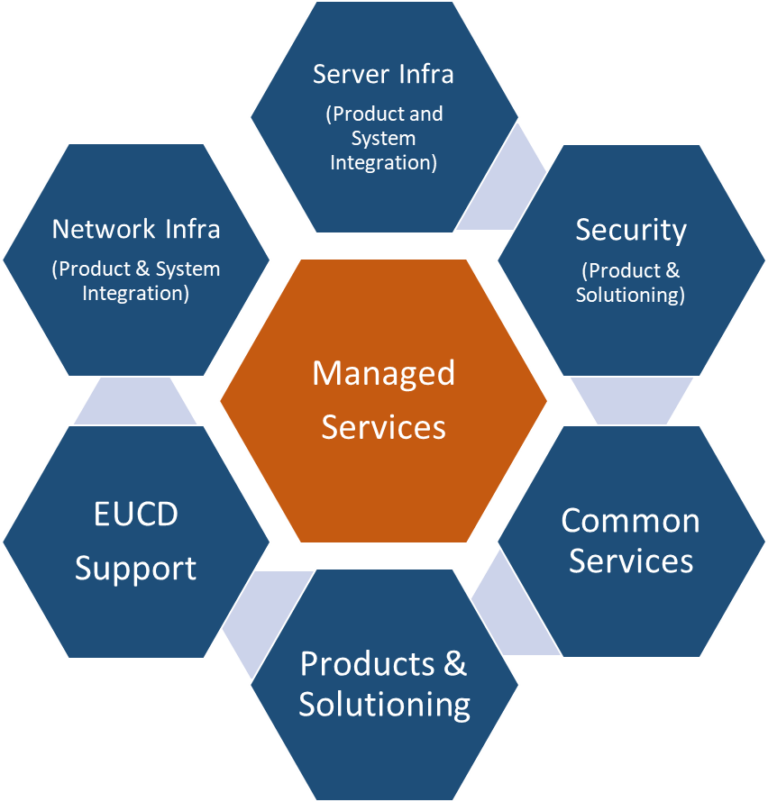
Managed Services
Normal 0 false false false EN-US X-NONE X-NONE /* Style Definitions */ table.MsoNormalTable {mso-style-name:"Table Normal"; mso-tstyle-rowband-size:0; mso-tstyle-colband-size:0; mso-style-noshow:yes; mso-style-priority:99; mso-style-parent:""; mso-padding-alt:0in 5.4pt 0in 5.4pt; mso-para-margin-top:0in; mso-para-margin-right:0in; mso-para-margin-bottom:10.0pt; mso-para-margin-left:0in; line-height:115%; mso-pagination:widow-orphan; font-size:11.0pt; font-family:"Calibri","sans-serif"; mso-ascii-font-family:Calibri; mso-ascii-theme-font:minor-latin; mso-hansi-font-family:Calibri; mso-hansi-theme-font:minor-latin; mso-bidi-font-family:"Times New Roman"; mso-bidi-theme-font:minor-bidi;}
Overview of Managed Services
A structured approach to Managed Services optimizes operations, increases efficiency, and provides comprehensive support to clients. This section highlights essential services like patch management and account control, critical for maintaining security and operational integrity.
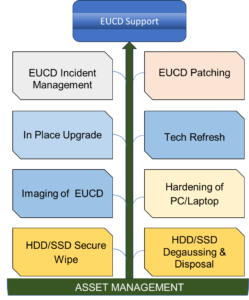
EUCD Managed
EUCD Services
End User Computing Support
EUCD Support
At Giganex, our experience Desktop Engineers will troubleshoot problems faced by users. Advise users on best practices, simple troubleshooting geeks, etc..
Patch Deployment
At Giganex, our experience engineers can deploy patches via remotely with relevant tools or deploy patches manually onsite. Generate reports and analyze trend to ensure proactive measures are taken.
In Place Upgrade (IPU)
Giganex Engineers are also well trained to conduct In Place upgrade for Operating System versions to keep up with the service lifetime.
Imaging & Tech Refresh
Giganex Engineers can create base image and replicate the imaging to multiple machines. Engineers can also refresh the old machines with the newly imaged machines.
Hardening of EUCD
Giganex Engineers can Customize the hardening according to the security needs of the organization.
Secure Wipe, Degaussing & Disposal
Giganex have the capabilities to do secure wipe the HDD/SSD. We are also able to Degauss the secured wiped HDD/SDD and Dispose them.
Common Services
We provide comprehensive IT support services that enhance operational efficiency, IT governance, and end-user experience.
How It Works
- Infrastructure Monitoring –Ensures health, performance, and reliability of your IT systems by continuously tracking key metrics such as server uptime, network performance, and resource utilization. This proactive approach helps identify issues before impacting operations, ensuring smooth business continuity. With real-time alerts and detailed insights, our monitoring service minimizes downtime and optimizes infrastructure efficiency.
- Software Packaging –Software packaging streamlines the deployment and installation of applications by creating standardized, easy-to-distribute packages. This ensures consistency across environments, reduces errors, and simplifies updates. Our service guarantees efficient, secure packaging for seamless application delivery.
- Centralized Patching –Centralized patching simplifies software updates by applying patches across all systems from a single control point. This ensures consistency, reduces security risks, and minimizes downtime. Our service automates patch deployment, keeping your infrastructure secure and up-to-date.
- Remote Desktop Support –Provides quick, efficient assistance by allowing engineers to access and troubleshoot systems remotely. This service minimizes downtime and resolves issues without the need for on-site visits. Our experts ensure smooth, uninterrupted operations with real-time support.
- Project Management Office –PMO ensures standardized processes, improving project consistency and delivery. It enhances resource management and provides valuable oversight, reduces risks, and improves project success rates.
- Servicedesk Support –Provide single point of contact for users to obtain first level IT support. Provide self-help advise and track all incidents closely to resolve and enhance operational capabilities.
- Reporting –Provide regular reports on contract obligations and KPIs to ensure transparency in operations management and data Analyzation.
- SOC & NOC Operations –NOC operations provides centralizes visibility, enhances network management, and improves efficiency and proper resources utilization. SOC strengthens network defense capabilities and optimizes workflows. Additionally, it helps reduce costs while providing a more proactive security posture.
Infra Structure Managed
System Infra Services.
Server Infrastructure Management

- System Updates and Patch Management:
- Regularly apply OS and software updates.
- Test patches in staging environments before deployment.
- Monitor security bulletins for relevant updates.
- Backup and Recovery:
- Implement regular backup schedules for critical data and system configurations.
- Ensure disaster recovery plans are in place and regularly tested.
- Capacity Planning and Scaling:
- Plan for future resource needs based on system growth and performance trends.
- Scale resources (CPU, RAM, storage) or migrate to more powerful hardware/virtual environments as necessary.
- Installation and Configuration:
- Deploy and configure physical and virtual servers.
- Install operating systems and necessary software.
- Set up server monitoring and alert systems.
- Performance Monitoring and Optimization:
- Monitor system performance (CPU, memory, disk usage, network).
- Analyze logs to identify bottlenecks or issues.
- Tune system configurations for optimal performance.
- Security Management:
- Configure firewalls, anti-malware software, and intrusion detection systems (IDS).
- Ensure server access is restricted with secure authentication mechanisms.
- Conduct regular security audits and vulnerability assessments.
Storage Management
- Capacity Management:
- Monitor and analyze storage usage and ensure that sufficient capacity is available.
- Implement storage quotas and policies for file systems or databases.
- Data Backup and Archiving:
- Implement backup policies for data storage.
- Archive old or infrequently accessed data to reduce storage usage on primary systems.
- Data Security:
- Encrypt sensitive data stored on disks.
- Ensure proper access control and auditing of storage resources.
- Data Redundancy and Replication:
- Ensure data redundancy by configuring RAID arrays or storage replication.
- Set up network-attached storage (NAS) or storage area network (SAN) solutions for large-scale environments.
- Disk Performance Monitoring:
- Monitor disk I/O performance, fragmentation, and disk health (e.g., using SMART tools).
- Optimize storage for high-performance or high-availability needs.
Database Management (DB)

- Installation and Configuration:
- Set up and configure database servers (SQL, NoSQL, etc.).
- Establish database instances and configure replication, clustering, and failover mechanisms.
- Performance Tuning:
- Monitor database performance (query execution times, indexing, resource usage).
- Optimize queries, indexes, and database configurations to improve performance.
- Ensure proper database schema design and normalization.
- Backup and Restore:
- Implement regular database backups (full, incremental, and differential).
- Test and verify backup integrity to ensure data can be restored when needed.
- Disaster Recovery:
- Set up and maintain database replication and clustering for high availability.
- Develop and test recovery procedures in case of data loss or corruption.
- Database Upgrades and Patching:
- Keep database systems up to date with the latest patches and updates.
- Plan and test database version upgrades in a controlled environment.
- Security:
- Enforce access control policies and role-based access.
- Encrypt sensitive data, both in transit and at rest.
- Regularly audit user activity and database access.
Active Directory (AD) Management

- Access Control and Permissions:
- Define and manage permissions for users and groups on network resources (files, applications, etc.).
- Implement least-privilege access principles and regularly audit permissions.
- Monitoring and Troubleshooting:
- Use tools like Active Directory Administrative Center, PowerShell scripts, and Event Viewer to monitor AD health and troubleshoot issues.
- Resolve issues related to AD replication, login failures, and GPO application problems.
- Security and Compliance:
- Implement security policies for password management, lockout policies, and multi-factor authentication (MFA).
- Regularly audit AD logs for unusual activities or potential security breaches.
- Backup and Restore:
- Regularly back up Active Directory data, including system state and configurations.
- Plan and test restoration procedures for recovering from AD failures.
- Domain Controllers and Replication:
- Maintain and monitor the health of Domain Controllers (DCs).
- Ensure proper AD replication between multiple DCs for high availability.
- User and Group Management:
- Create, modify, and delete user accounts and groups.
- Implement group policies (GPOs) to control user and computer behavior across the network.
- Manage organizational units (OUs) for delegation of administrative tasks.
Network Services
Network Management ensures the seamless operation, security, and optimization of your organization’s network infrastructure. Our comprehensive suite of services includes network design and implementation, proactive monitoring, security management, performance optimization, and troubleshooting. With a focus on scalability and reliability, we aim to deliver robust network solutions that support business growth while minimizing downtime and enhancing user experience. Whether it’s managing on-premises systems, cloud integrations, or ensuring compliance, our Network Management services are tailored to meet the unique needs of your business, backed by expert support and industry best practices.
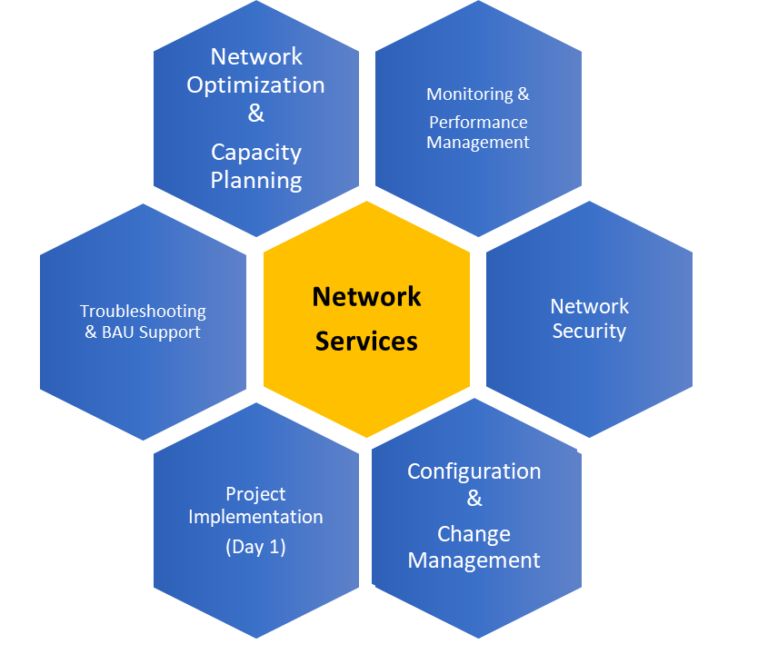

Network Services
- 1. Network Monitoring
- - Continuous monitoring of network performance and traffic to identify issues.
- - Real-time alerts for network anomalies or failures.
- 2. Network Configuration & Configuration management
- - Setup and configuration of network devices (routers, switches, firewalls).
- - Standardization across the network.
- 3. Network Documentation
- - Creating and maintaining network diagrams and documentation for architecture and configurations.
- - Regular updates to ensure accuracy and compliance.
- 4. Bandwidth Management
- - Monitoring and optimizing network bandwidth to ensure optimal performance.
- - Prioritizing critical applications and traffic.
- 5. Network Compliance Management
- - Ensuring network configurations and practices comply with industry standards and regulations (e.g., GDPR, HIPAA).
- - Conducting regular audits and compliance checks.
- 6. Network Security
- - Implementation of firewalls, VPNs, and intrusion detection/prevention systems (IDS/IPS).
- - Regular vulnerability assessments and patch management for network devices.
- 7. Network Performance Optimization
- - Analyzing network data to optimize routing, traffic flow, and reduce latency.
- - Ensuring Quality of Service (QoS) for high-priority applications.
- 8. Network Capacity Planning
- - Forecasting future network requirements based on growth trends.
- - Ensuring the network infrastructure can scale effectively.
- 9. Wi-Fi Management
- - Configuration and management of wireless networks, ensuring security and performance.
- - Regular Wi-Fi site surveys to optimize coverage and signal strength.
- 10. Disaster Recovery Planning
- - Developing and testing network backup and recovery plans.
- - Ensuring redundancy and high availability to minimize downtime during disruptions.
- 11. VPN Setup and Management
- - Configuration and management of Virtual Private Networks (VPN) for secure remote access.
- - Regular monitoring of VPN performance and security.
- 12. Network Upgrades and Patching
- - Regular updates and patching of network infrastructure to ensure security and stability.
- - Managing lifecycle and end-of-life upgrades for network equipment.
- 13. Incident Management
- - Managing network incidents and outages, ensuring timely resolution.
- - Post-incident analysis and reporting to improve future response.
